I’ve been busy and remiss in blogging and this is something I was hoping to publish a while ago, so I give you… a review of the onlykey.
The onlykey is a USB2 connectable hardware security key. Many of you may know yubikeys, this is a competitor to those, with some advantages and disadvantages.
Ordering was simple, I just ordered one via amazon and had it 2 days later. You can also order directly from the onlykey website.
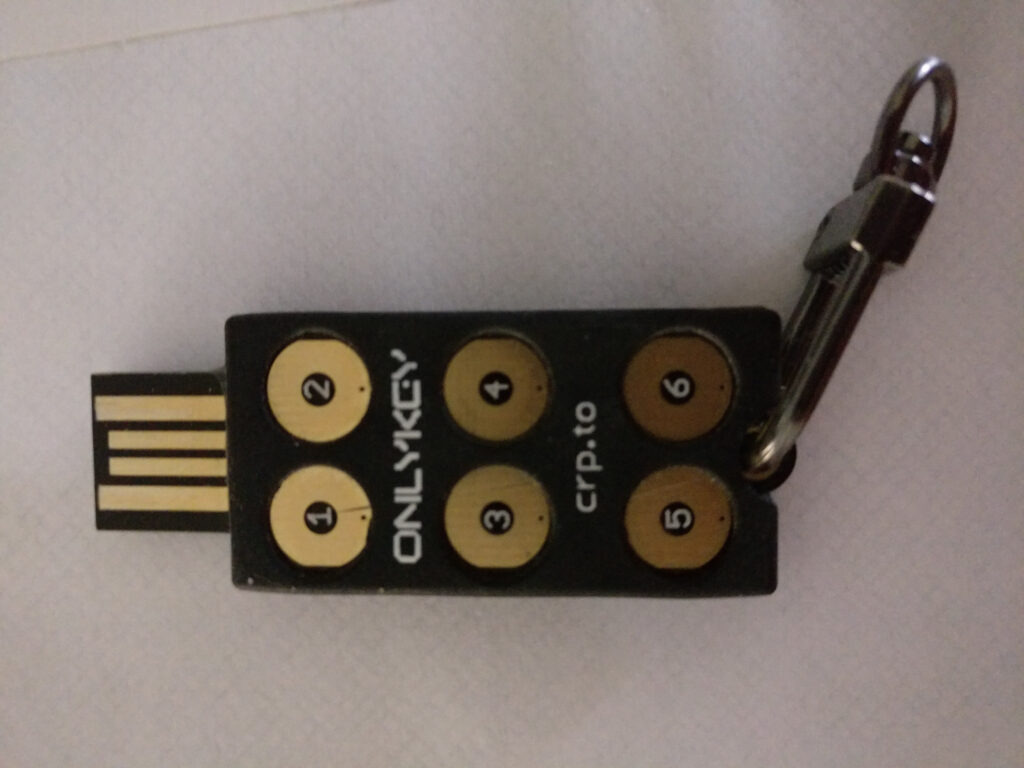
Right away you will note that this doesn’t have just one key like the yubikeys do, but instead has 6 of them. Additionally, it’s got a colored LED underneath, which shines green when it’s unlocked, flashes red when you enter an incorrect pin, etc. The idea here is that the key will be completely locked and useless to others until its plugged in and a correct pin is entered (yes, there’s more than one correct pin 🙂 This key only comes in USB2 form as they say USBC would be too fragile. You can of course use a USB2 -> USBC adapter.
There’s Several ways to manage the key:
- A chrom(imum) “app”. (Although chrome is discontinuing these)
- A “snap”
- A debian .deb package
So, thats not great for Fedora. I tried to get the snap working, but it failed. I tried to use the chrome app, but thats how I found that they are dropping those, so I went with the debian package unpacked and just using the application from there. The app is open source if anyone wants to package it up: https://github.com/trustcrypto/OnlyKey-App (It’s npm based)
Right off the bat I hit an issue. My onlykey had old firmware and it was old enough that the app was unable to update it, so I had to monkey around with “Teensy loader” to upgrade the firmware. At one point the key stopped even lighting up and I asked for help on the onlykey discussion group. They had someone answer me pretty quickly and I found that I wasn’t properly shorting the two contacts on each end of the key to put it in ‘upload firmware mode’. After I did that I managed to update to the new firmware and everything was smooth sailing after that. I really hope they have all their existing stock updated now so no one else should have to go through this. 🙂 Just look at these little contacts you have to short together while pressing the upload button on Teensy Loader! I managed to do it with a hanger from a xmas tree ornament finally:

There’s a sort of soft rubber case around the key, you can get all kinds of colors (I just stuck with black). It also comes with the handy little carribeener to attach it to your keychain or whatever.
So, once you have the firmware somewhat up to date, you can run the app. It will also update firmware as long as it’s not too old. The firmware is open source: https://github.com/trustcrypto/OnlyKey-Firmware
On your first run (or if you factory wipe it), you have to do a bit of setup. You can enter 2 profile pins (sequences of buttons). They suggest that this might be ‘work’ and ‘home’, but you could use them for whatever you like. You can also enter a ‘self destruct’ profile pin, which wipes back to factory settings if you enter it. You can also tell it to do this if someone enters the wrong pin 10 times, but it will flash red and stop taking input after 3 failed pins. So to wipe it this way you have to enter 3 wrong pins, remove, insert, 3 more wrong pins, remove, insert 3 more wrong pins, remove, insert, 1 more wrong pin. You can also load a firmware called the “International Travel Edition” that has no encryption at all (it’s only protected by the pin).
Once you have your profiles setup you can configure what you want in the slots. There’s actually 12 slots because (just like yubikeys) there is long press and short press on each button. You can assign whatever you like to those 24 slots (12 for each profile). You can do TOTP, U2F, Yubikey HOTP, username/password, tabs or returns, all kinds of things:
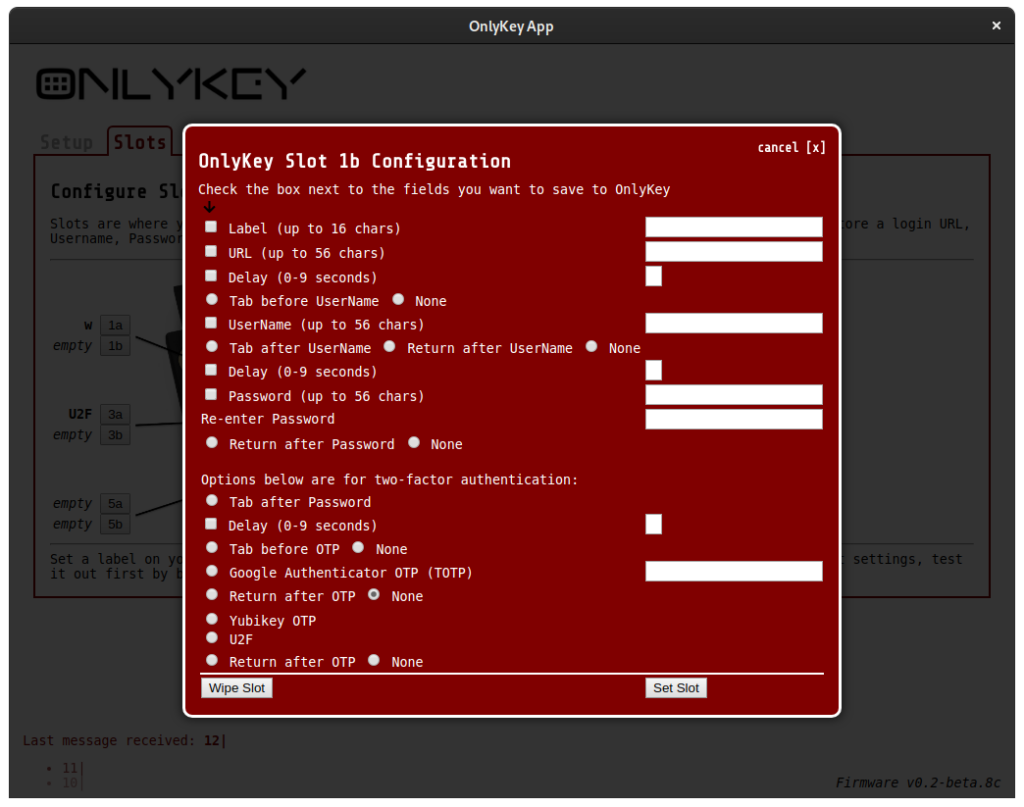
You can do encrypted backups of the contents of the key and of course restore them. There’s also some misc settings like how bright the LED is or how fast the keyboard types or what keyboard layout it uses. There’s some integration with keybase.io to do encrypted files/messages transfer.
Finally, there’s some advanced prefs about yubikeys and U2F tokens. I was confused by these at devconf, but the manual explains: https://docs.crp.to/usersguide.html#Yubico-one-time-password basically you have to run yubikey-personalize and have it generate “Public Identify, Private Identity, and Secret Key” which you then enter into the onlykey app. I can only assume they couldn’t just do this due to legal concerns. The U2F prefs are there because:
For the attestation certificates OnlyKey comes with a default attestation certificate and signing key and also allows users or enterprises to import their own attestation certificate/key. This feature allows organizations to only permit FIDO2 keys issued by the organization to be used. Importing attestation certificates and signing keys can be done in the OnlyKey app.
The manual is pretty easy to read and covers all this better than I can probibly. So, on to the actual reviewing:
First the good:
- Open source firmware and app!
- Nice to know that if someone stole it, they would not be able to access anything using it.
- Seems to work fine for U2F/webauthn, TOTP, HOTP and user/pass.
- The LED light is nice to know what state it’s in.
- I like being able to do encrypted backups.
- Having a bunch more slots is nice (If you forget which is which, you can press and hold down the 2 button for 5+ seconds and it will print out the labels you gave the slots).
Now the not so good:
- You can set a timeout where the key will lock after X minutes. It works and the LED goes off but the application if you have it open will happily think it’s still talking to the unlocked key (until you try and do something then it errors).
- You can sort of use it for keeping your ssh private key, but not easily. You have to import a key (using only very specific ecc curves) and then use a ‘onlykey-agent’ instead of normal ssh agent. This is a fork of another project and hasn’t been updated from that fork for like 4 years, which is really not encouraging. 🙁
- It’s a bit odd trying to type in your pin at say a coffee shop or table with a bunch of co-workers around. It seems like you can’t really hide what you are pressing. Still it is more secure than just any unlocked always token.
For me personally, the lack of a nice way to use it for storing my ssh private key is somewhat of a deal breaker. I really really don’t want that key to get out (even though it is passphrase protected). My current yubikey was able to generate it on key and keep it always stored there. If I didn’t care so much about ssh keys I might well move to using the onlykey day to day. If I traveled much I definitely would look at using it while traveling.